We protect users' funds and privacy with layered security controls and strict operational procedures. Our systems and processes undergo multiple audits every year.
that drive results
We use hardened hardware security modules (HSMs) to store master keys, derive signing keys, and run the policy engine.
Multi-party approval uses off-chain quorums backed by hardware tokens. This keeps governance logic invisible on-chain.
Key generation and backups procedures follow the CMTA DACS standard and are ISAE 3402-audited.
Support for hot and cold setups, always with in-HSM keys.




















Our IT infrastructure runs on Tier III and IV data centers in Switzerland.
Strong authentication and segregation of duty across the board. 24/7 security monitoring and IR.
Audited SSDLC processes. CI/CD pipelines integrating automated scans and supply-chain controls.
Supplier due diligence and monitoring with joint security tests and on-site assessments.




















Three lines of defense model: process owners, risk & compliance, internal & external audit.
All staff pass background checks and receive training in security, with focused sessions on data protection, OPSEC, cryptography.
Processes and policies aligned with or exceeding banking standard, from access and change management to BCP and threat intelligence.
Multiple DRP tests every year, incl. data center failover and signing keys recovery.




















Independent teams assess our systems: pentests, code audits, red teaming. Reports are shared with clients.
Users of Taurus-PROTECT clients can access all its source code and organize third-part tests.
Critical software built under auditor oversight, using reproducible builds. Certification report shared with clients.
At least 10 third-party security tests every year.




















Taurus Labs runs applied research projects and collaborates with leading academics, practitioners, and blockchain organizations.
Topics include: multi-party computation, hardware security, post-quantum cryptography, zero-knowledge proofs, private tokens, and automation.
We publish open-source software, research papers, and speak at global events.




















Compliance and certifications
Standard for risk assurance and internal controls
Top-tier security standard for HSM devices
CMTA Digital Assets Custody Standard, ensuring safe custody procedures and technology security
The globally trusted standard for information security

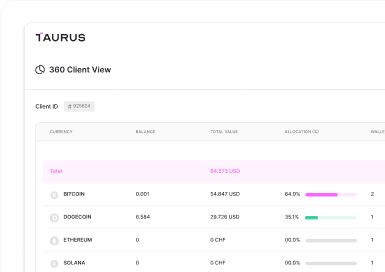
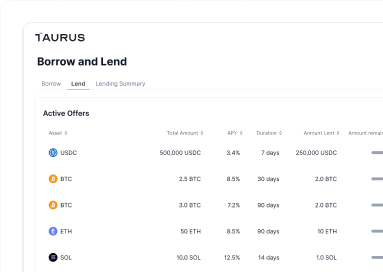



 Taurus-PROTECT Custody
Taurus-PROTECT Custody
 Taurus-CAPITAL Tokenization
Taurus-CAPITAL Tokenization
 Taurus-PRIME Trading
Taurus-PRIME Trading
 Taurus-NETWORK Collateral
Taurus-NETWORK Collateral